by Joche Ojeda | Jul 28, 2024 | PropertyEditors, XAF
Introduction
The eXpressApp Framework (XAF) from DevExpress is a versatile application framework that supports multiple UI platforms, including Windows Forms and Blazor. Maintaining separate property editors for each platform can be cumbersome. This article explores how to create unified property editors for both Windows Forms and Blazor by leveraging WebView for Windows Forms and the Monaco Editor, the editor used in Visual Studio Code.
Blazor Implementation
Windows forms Implementation
Prerequisites
Before we begin, ensure you have the following installed:
- Visual Studio 2022 or later
- .NET 8.0 SDK or later
- DevExpress XAF 22.2 or later
Step 1: Create a XAF Application for Windows Forms and Blazor
- Create a New Solution:
- Open Visual Studio and create a new solution.
- Add two projects to this solution:
- A Windows Forms project.
- A Blazor project.
- Set Up XAF:
- Follow the DevExpress documentation to set up XAF in both projects. Official documentation here
Step 2: Create a Razor Class Library
- Create a Razor Class Library:
- Add a new Razor Class Library project to the solution.
- Name it XafVsCodeEditor.
- Design the Monaco Editor Component:
We are done with the shared library that we will reference in both Blazor and Windows projects.
Step 3: Integrate the Razor Class Library into Windows Forms
- Add NuGet References:
- In the Windows Forms project, add the following NuGet packages:
- Microsoft.AspNetCore.Components.WebView.WindowsForms
- XafVsCodeEditor (the Razor Class Library created earlier).
- You can see all the references in the csproj file.
- Change the Project Type: In order to add the ability to host Blazor components, we need to change the project SDK from Microsoft.NET.Sdk to Microsoft.NET.Sdk.Razor.
- Add Required Files:
- wwwroot: folder to host CSS, JavaScript, and the index.html.
- _Imports.razor: this file adds global imports. Source here.
- index.html: one of the most important files because it hosts a special blazor.webview.js to interact with the WebView. See here.
Official Microsoft tutorial is available here.
Step 4: Implementing the XAF Property Editors
I’m not going to show the full steps to create the property editors. Instead, I will focus on the most important parts of the editor. Let’s start with Windows.
In Windows Forms, the most important method is when you create the instance of the control, in this case, the WebView. As you can see, this is where you instantiate the services that will be passed as a parameter to the component, in our case, the data model. You can find the full implementation of the property editor for Windows here and the official DevExpress documentation here.
protected override object CreateControlCore()
{
control = new BlazorWebView();
control.Dock = DockStyle.Fill;
var services = new ServiceCollection();
services.AddWindowsFormsBlazorWebView();
control.HostPage = "wwwroot\\index.html";
var tags = MonacoEditorTagHelper.AddScriptTags;
control.Services = services.BuildServiceProvider();
parameters = new Dictionary<string, object>();
if (PropertyValue == null)
{
PropertyValue = new MonacoEditorData() { Language = "markdown" };
}
parameters.Add("Value", PropertyValue);
control.RootComponents.Add<MonacoEditorComponent>("#app", parameters);
control.Size = new System.Drawing.Size(300, 300);
return control;
}
Now, for the property editor for Blazor, you can find the full source code here and the official DevExpress documentation here.
protected override IComponentModel CreateComponentModel()
{
var model = new MonacoEditorDataModel();
model.ValueChanged = EventCallback.Factory.Create<IMonacoEditorData>(this, value => {
model.Value = value;
OnControlValueChanged();
WriteValue();
});
return model;
}
One of the most important things to notice here is that in version 24 of XAF, Blazor property editors have been simplified so they require fewer layers of code. The magical databinding happens because in the data model there should be a property of the same value and type as one of the parameters in the Blazor component.
Step 5: Running the Application
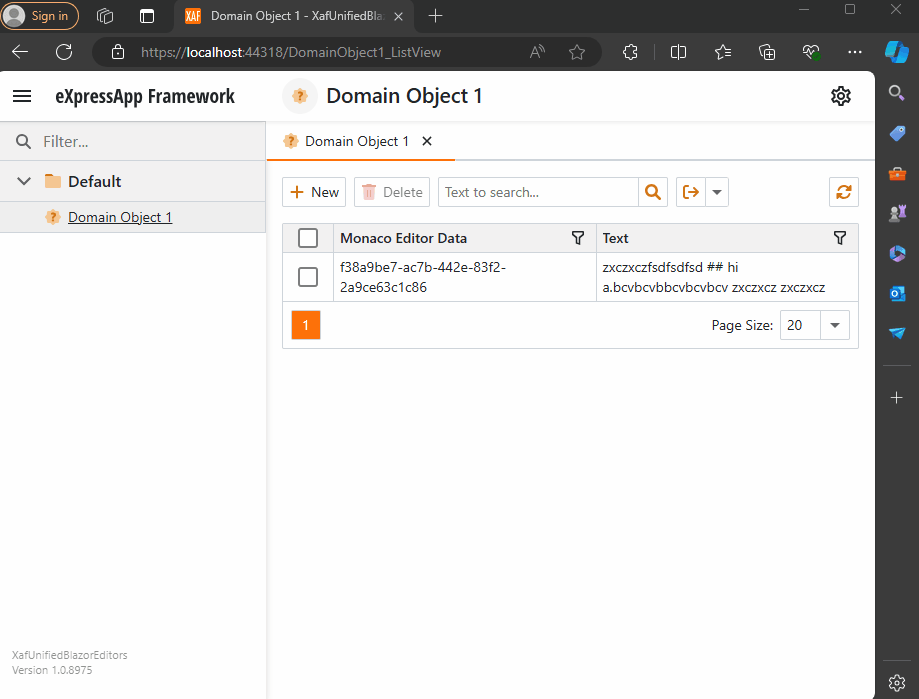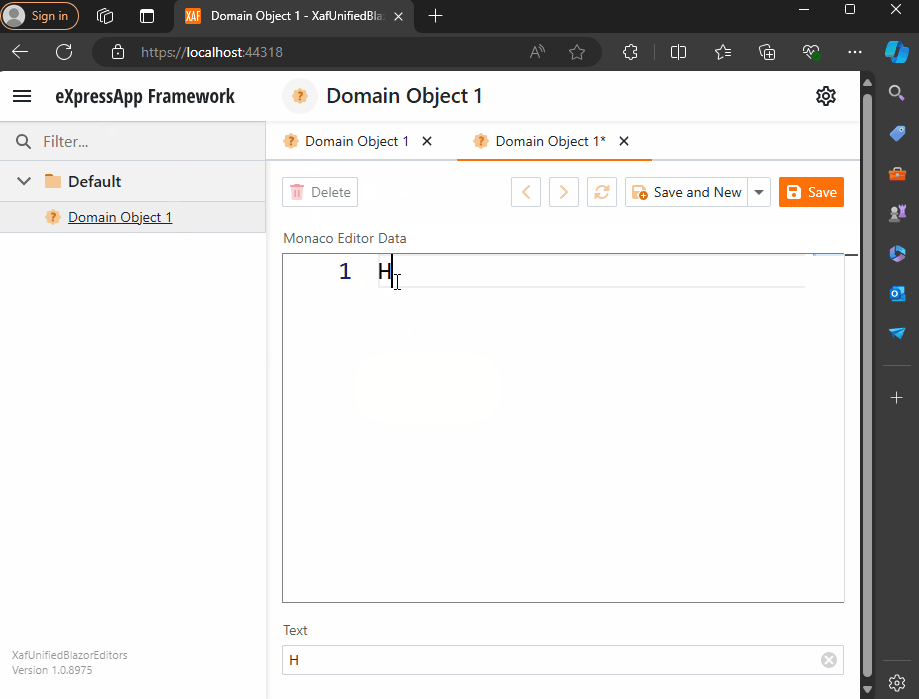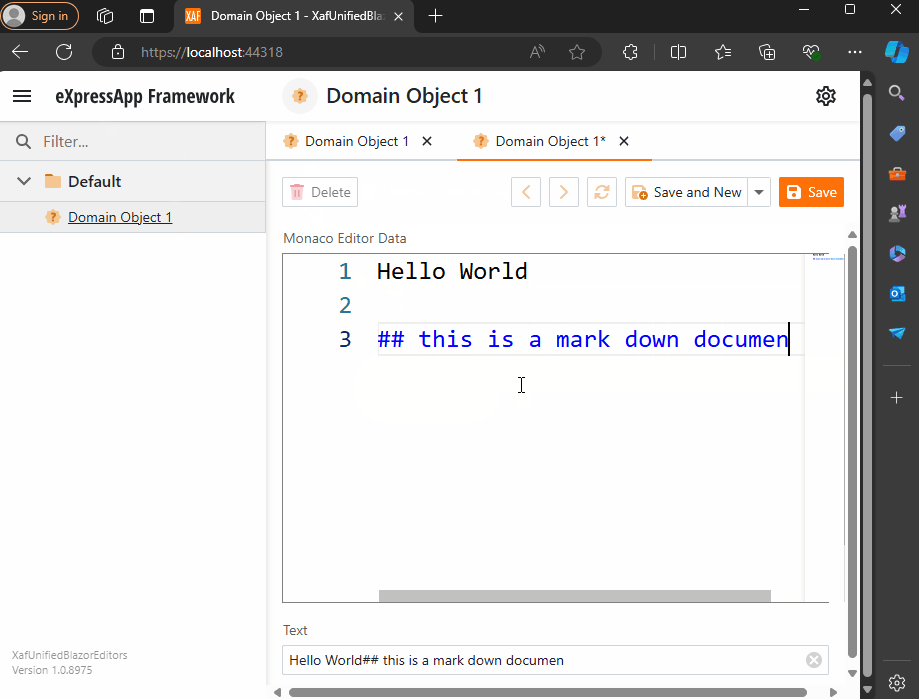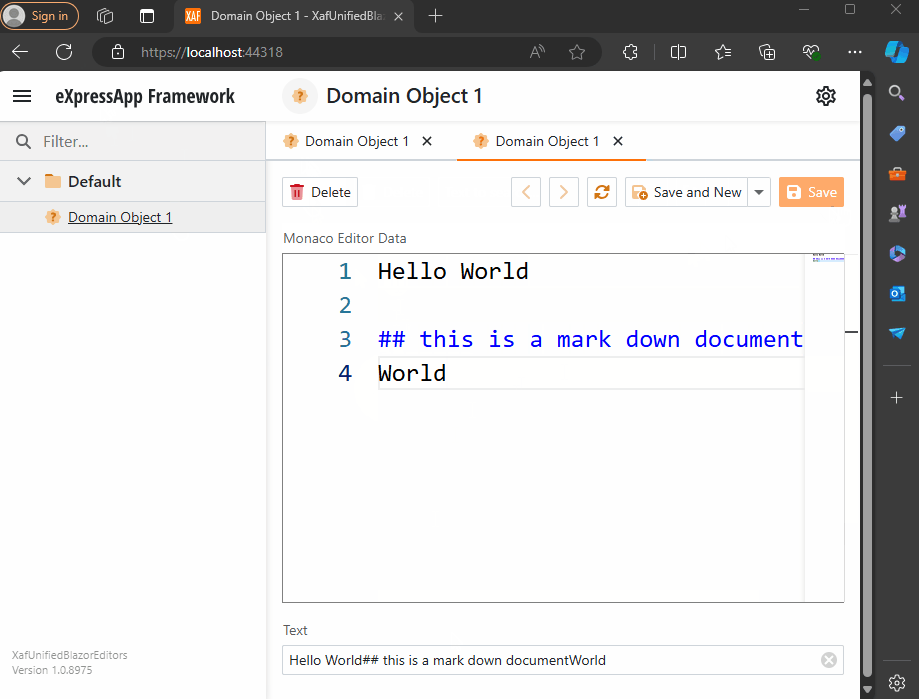
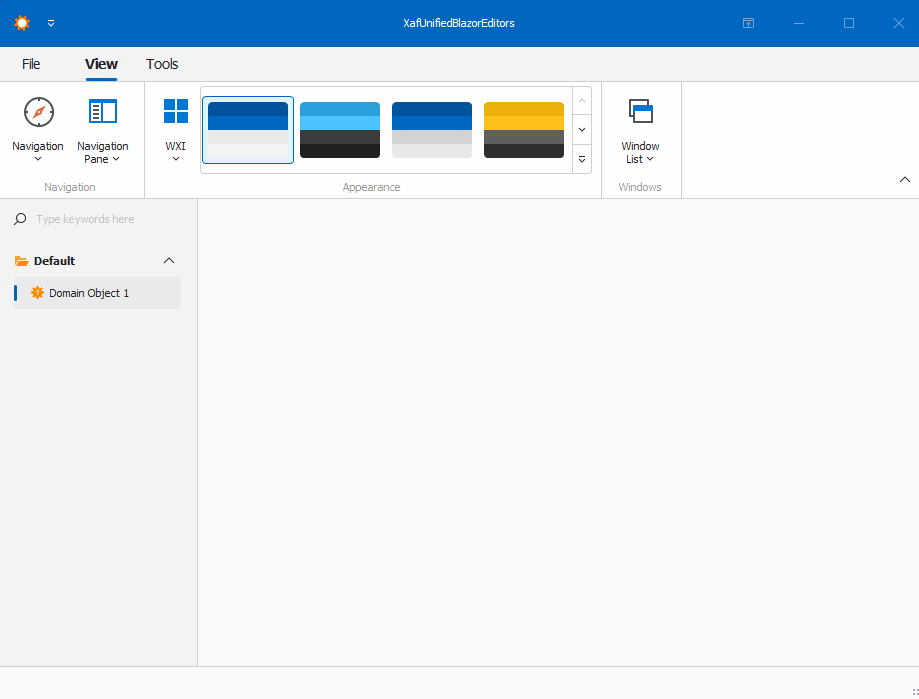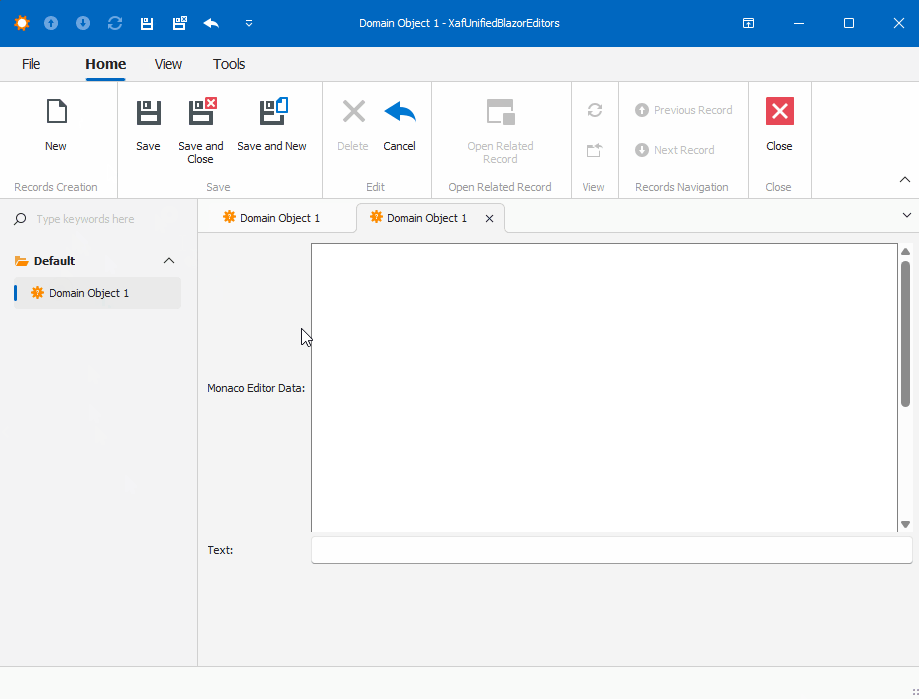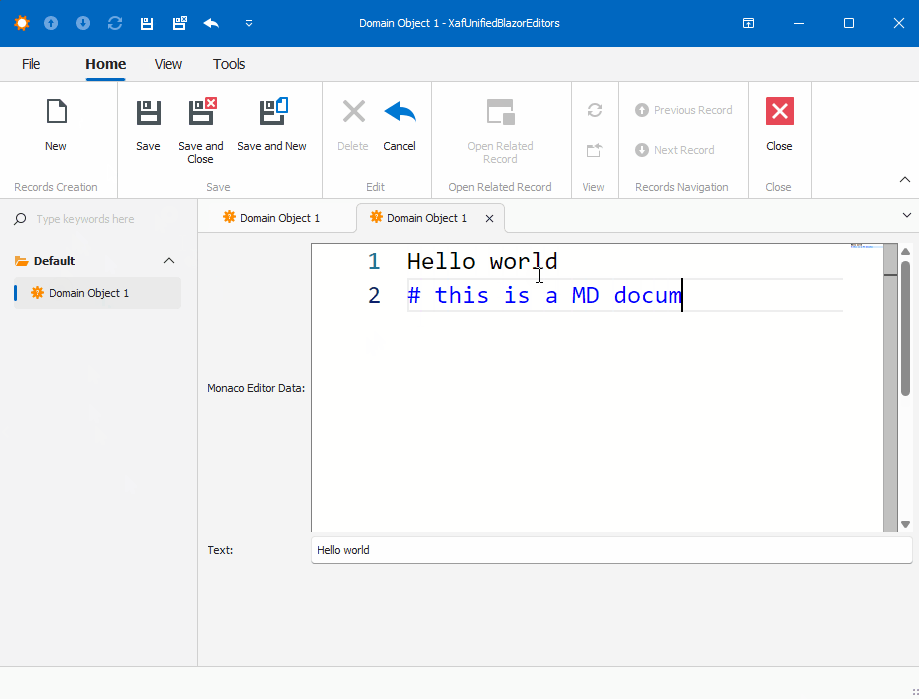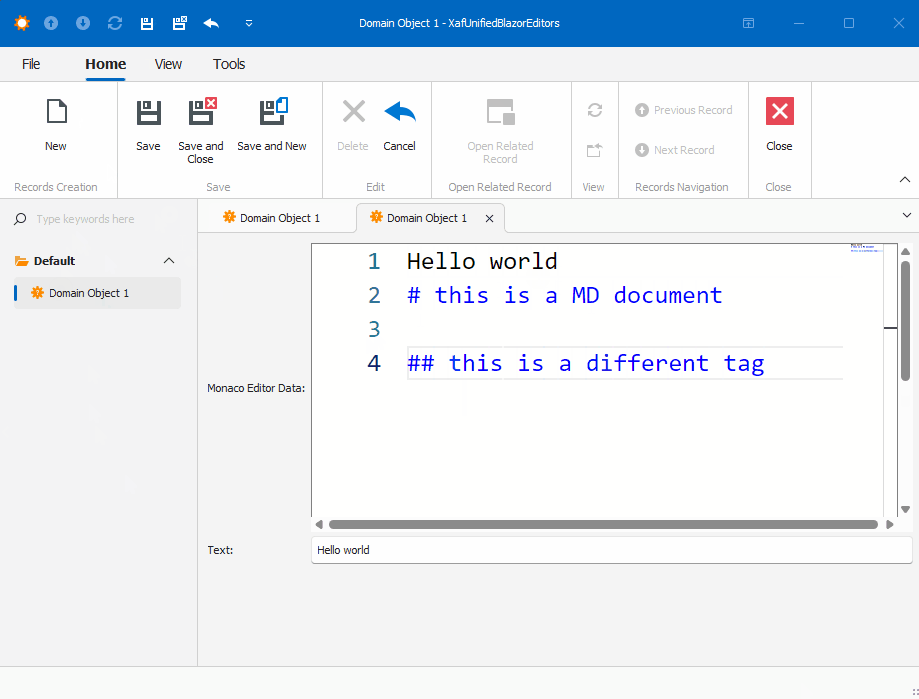
Before we run our solution, we need to add a domain object that implements a property of type IMonacoData, which is the interface we associated with our property editor. Here is a sample domain object that has a property of type MonacoEditorData:
[DefaultClassOptions]
public class DomainObject1 : BaseObject, IXafEntityObject
{
public DomainObject1(Session session) : base(session) { }
public override void AfterConstruction()
{
base.AfterConstruction();
}
MonacoEditorData monacoEditorData;
string text;
public MonacoEditorData MonacoEditorData
{
get => monacoEditorData;
set => SetPropertyValue(nameof(MonacoEditorData), ref monacoEditorData, value);
}
[Size(SizeAttribute.DefaultStringMappingFieldSize)]
public string Text
{
get => text;
set => SetPropertyValue(nameof(Text), ref text, value);
}
public void OnCreated()
{
this.MonacoEditorData = new MonacoEditorData("markdown", "");
MonacoEditorData.PropertyChanged += SourceEditor_PropertyChanged;
}
void IXafEntityObject.OnSaving()
{
this.Text = this.MonacoEditorData.Code;
}
void IXafEntityObject.OnLoaded()
{
this.MonacoEditorData = new MonacoEditorData("markdown", this.Text);
MonacoEditorData.PropertyChanged += SourceEditor_PropertyChanged;
}
private void SourceEditor_PropertyChanged(object sender, PropertyChangedEventArgs e)
{
this.Text = this.MonacoEditorData.Code;
}
}
As you can see, DomainObject1 implements the interface IXafEntityObject. We are using the interface events to load and save the content of the editor to the text property.
Now, build and run the solution. You should now have a Windows Forms application that hosts a Blazor property editor using WebView and the Monaco Editor, as well as a Blazor application using the same property editor.
You can find a working example here.
Conclusion
By leveraging WebView and the Monaco Editor, you can create unified property editors for both Windows Forms and Blazor in XAF applications. This approach simplifies maintenance and provides a consistent user experience across different platforms. With the flexibility of Blazor and the robustness of Windows Forms, you can build powerful and versatile property editors that cater to a wide range of user needs.

by Joche Ojeda | Jul 6, 2024 | Uncategorized
AI Integration and Future Plans
El Salvador has embarked on a remarkable journey of technological transformation under the leadership of President Nayib Bukele. Building on the momentum from its pioneering adoption of Bitcoin as legal tender, the nation is now setting its sights on integrating Artificial Intelligence (AI) into various sectors to foster innovation and growth. This article explores President Bukele’s vision for AI, the potential benefits and challenges, and the critical need for establishing robust AI legislation.
Government Vision for AI
President Bukele envisions a future where AI plays a central role in El Salvador’s development. In recent developments, he appointed Brian Roemmele, a renowned expert in voice technology and AI, as an AI advisor. Roemmele’s appointment highlights the government’s commitment to integrating AI to drive economic growth and educational opportunities, positioning El Salvador as a leader in the digital age[7][8][9].
Economic Growth: By fostering an environment conducive to AI innovation, El Salvador aims to attract tech companies and startups, thereby boosting economic growth and creating high-tech job opportunities.
Smart Governance: The integration of AI in government operations promises to enhance efficiency, transparency, and responsiveness, making public administration more effective and citizen-centric[28][30].
Global Competitiveness: Bukele’s vision includes positioning El Salvador as a leader in AI within Latin America, much like its pioneering role with Bitcoin. This involves not only adopting AI technologies but also setting standards that other countries can follow.
Potential Benefits and Challenges
The potential benefits of AI integration are immense:
Economic Benefits: AI can drive significant economic growth by improving productivity, fostering innovation, and creating new job sectors[28][30].
Social Benefits: AI can enhance the quality of life by improving healthcare, education, and public services, leading to a more inclusive and equitable society[27][29].
However, the challenges cannot be overlooked:
Ethical Concerns: Ensuring that AI systems are fair, transparent, and free from bias is crucial to prevent societal harm.
Data Privacy: Protecting the personal data of citizens is essential to maintain trust and prevent misuse.
Workforce Displacement: The transition to an AI-driven economy must be managed carefully to support workers displaced by automation through reskilling and education initiatives.
The Need for AI Legislation
To harness the full potential of AI while addressing its challenges, it is imperative to establish a comprehensive AI legal framework. This framework should cover several key areas:
1. Ethical Standards
- Transparency: AI developers must disclose methodologies and data sources to ensure clarity and trust.
- Accountability: Clear accountability mechanisms for AI decisions, especially in critical sectors like healthcare and finance.
- Fairness: Measures to prevent bias and ensure equitable treatment for all users of AI systems.
2. Data Protection
- Privacy Laws: Strengthened data privacy laws to safeguard citizens’ information.
- Consent: Ensuring individuals have control over their data, including the ability to opt-out of AI data processing.
3. Innovation Incentives
- Research Grants: Funding for AI research and development projects.
- Tax Breaks: Tax incentives for companies investing in AI technologies and infrastructure.
4. Workforce Transition
- Reskilling Programs: Programs to help workers displaced by AI acquire new skills and transition to new job opportunities in the AI sector.
- Education Initiatives: Integrating AI and digital literacy into the national education curriculum.
5. International Cooperation
- Standards Collaboration: Working with international bodies to adopt global AI standards and best practices.
- Regional Partnerships: Fostering regional cooperation in AI research and development.
Conclusion
El Salvador’s journey towards technological transformation continues with the integration of AI. By setting the rules for AI through robust legislation, El Salvador can ensure that it remains at the forefront of innovation in Latin America. The proposed AI legal framework not only addresses the ethical and practical challenges of AI but also positions the country as a leader in the digital future. As El Salvador charts this new course, the commitment to innovation and responsible governance will be key to its success.
This article outlines the government’s vision for AI in El Salvador, the potential benefits and challenges, and the critical need for AI legislation. It aims to inform and engage readers, encouraging them to support and contribute to the country’s digital future.
Related Articles
El Salvador: Digital Transformation Initiatives
El Salvador: The Implementation of Bitcoin as Legal Tender
El Salvador’s Technological Revolution

by Joche Ojeda | Jul 5, 2024 | El Salvador, Uncategorized
Partnerships with Tech Giants
El Salvador has embarked on an ambitious journey of digital transformation, significantly bolstered by strategic partnerships with leading technology companies. These collaborations have been pivotal in advancing the country’s technological landscape across various sectors.
One notable partnership is with Google, focusing on enhancing healthcare, education, and digital government services. Google’s involvement includes the deployment of cloud services to streamline government operations and the integration of AI tools to improve healthcare delivery. Through these initiatives, El Salvador aims to enhance the efficiency and accessibility of public services, ensuring that technology benefits all citizens.
In the education sector, partnerships with tech giants are transforming learning environments. Google Classroom and other digital platforms are being integrated into schools, enabling remote learning and enhancing the quality of education. These tools not only facilitate learning during crises like the COVID-19 pandemic but also prepare students for a digital future.
Development of Digital Infrastructure
Central to El Salvador’s digital transformation is the robust development of digital infrastructure. The government has made significant investments to ensure widespread internet access, recognizing it as a cornerstone for digital inclusion. Efforts include expanding broadband coverage to rural areas and implementing 5G technology in urban centers.
Digital payment systems have also seen substantial growth. The introduction of the Chivo Wallet, a government-backed digital wallet, marked a significant step in promoting cashless transactions. This initiative aligns with the broader goal of fostering a digital economy and reducing the reliance on traditional banking systems. Moreover, the Chivo Wallet’s integration with Bitcoin and other cryptocurrencies opens new avenues for financial inclusion and innovation.
E-government platforms are another critical component of this transformation. The government has launched various online portals to streamline public services, from tax filing to business registrations. These platforms not only enhance efficiency but also reduce bureaucratic hurdles, making it easier for citizens and businesses to interact with the government.
Efforts to Improve Digital Literacy
Recognizing that technological advancements are only as effective as the population’s ability to use them, El Salvador has prioritized digital literacy. The government, in collaboration with educational institutions and private sector partners, has launched comprehensive programs aimed at improving digital skills across the population.
For the general public, initiatives include community training programs and digital literacy campaigns. These efforts focus on teaching basic computer skills, internet navigation, and the safe use of digital tools. By equipping citizens with these skills, the government aims to ensure that everyone can participate in the digital economy and access online services.
In the education sector, digital literacy is being integrated into the national curriculum. Schools are now equipped with modern technology, and teachers receive training on digital teaching methods. This approach not only prepares students for future job markets but also fosters a culture of innovation and technological proficiency from a young age.
Government employees are also a focus of digital literacy efforts. Specialized training programs have been developed to enhance the digital skills of public sector workers. These programs aim to improve the efficiency of government operations and ensure that public servants can effectively use new technologies in their daily tasks.
Conclusion
El Salvador’s digital transformation under President Nayib Bukele is a multifaceted effort encompassing strategic partnerships, infrastructure development, and comprehensive digital literacy programs. By working with tech giants like Google, investing in digital infrastructure, and prioritizing digital education, the country is laying a strong foundation for a technologically advanced future. These initiatives not only improve the quality of life for Salvadorans but also position the country as a leader in digital innovation within Latin America. As El Salvador continues to embrace digital transformation, it serves as a compelling case study for other nations seeking to navigate the complexities of the digital age.
Related Articles
El Salvador: The Implementation of Bitcoin as Legal Tender
El Salvador’s Technological Revolution

by Joche Ojeda | Jul 4, 2024 | Bitcoin, El Salvador
Background
Before delving into the specifics of Bitcoin’s adoption, it’s crucial to understand the economic landscape of El Salvador. Historically, the country has faced significant economic challenges, including high poverty rates, limited access to financial services, and a heavy reliance on remittances, which account for about 20% of its GDP. Since 2001, El Salvador has used the US dollar as its official currency, which has provided stability but also limited monetary policy options for the government.
Bitcoin Law
On June 9, 2021, El Salvador made headlines worldwide by becoming the first country to adopt Bitcoin as legal tender. The Bitcoin Law, proposed by President Nayib Bukele and swiftly passed by the Legislative Assembly, mandates that Bitcoin must be accepted as a form of payment by all businesses and allows it to be used for all debts, public or private. The law’s key provisions include:
- Mandatory Acceptance: All economic agents must accept Bitcoin as payment when offered by the buyer.
- Tax Contributions: Tax contributions can be paid in Bitcoin.
- Pricing: Prices can be expressed in Bitcoin.
- Exchanges: Exchanges between Bitcoin and the US dollar will be exempt from capital gains tax.
- Government Support: The government will promote the necessary training and mechanisms so that the population can access Bitcoin transactions.
The initial public response was mixed. While some saw it as a groundbreaking move to modernize the economy, others were skeptical about the volatility of Bitcoin and its potential impacts on everyday transactions.
Implementation
The implementation of Bitcoin involved several key steps:
- Chivo Wallet: The government developed the Chivo Wallet, a digital wallet that allows users to store and transact in Bitcoin and US dollars. To incentivize adoption, each user who signed up received $30 worth of Bitcoin.
- Bitcoin ATMs: A network of Bitcoin ATMs was established across the country to facilitate the exchange between Bitcoin and US dollars.
- Government Investments: The Salvadoran government made several Bitcoin purchases, intending to stabilize the market and show confidence in the new system.
Despite initial technical glitches and skepticism, the government continued to promote Bitcoin adoption through educational campaigns and infrastructure development.
Impact
Economic Impact
- Financial Inclusion: Bitcoin has provided an opportunity for financial inclusion, particularly for the unbanked population. With around 70% of Salvadorans lacking access to traditional banking services, Bitcoin offers an alternative means of participating in the economy.
- Remittances: The use of Bitcoin for remittances has the potential to reduce transaction fees and speed up transfer times, benefiting many Salvadoran families who rely on money sent from abroad.
- Investment and Tourism: The Bitcoin initiative has attracted international attention, potentially boosting tourism and foreign investment. The country has seen a surge in crypto-related tourism, with enthusiasts visiting to experience a Bitcoin-driven economy firsthand.
Social Impact
- Education and Awareness: The push for Bitcoin has necessitated widespread educational efforts to ensure that the population understands how to use and benefit from digital currency. This has sparked broader discussions about financial literacy and digital technologies.
- Public Sentiment: Public opinion remains divided. While some embrace the innovation, others fear the volatility of Bitcoin and the implications for price stability and everyday transactions.
Conclusion
El Salvador’s bold move to adopt Bitcoin as legal tender marks a significant milestone in its technological transformation. While the long-term effects are still unfolding, this initiative positions the country at the forefront of digital currency adoption. The next steps involve addressing the challenges of volatility, continuing to educate the population, and monitoring the broader economic impacts. As the world watches, El Salvador’s experiment with Bitcoin will provide valuable lessons for other nations considering similar paths.
Related Articles
El Salvador’s Technological Revolution

by Joche Ojeda | Jul 3, 2024 | A.I, Blockchain, El Salvador
El Salvador, my birthplace, has recently emerged as a focal point for technological innovation under the leadership of President Nayib Bukele. Born in Suchitoto during the civil war and now living as a digital nomad in Saint Petersburg, Russia, I have witnessed El Salvador’s transformation from a distance and feel compelled to share its story. This article is the first in a series exploring how blockchain technology, financial services, and artificial intelligence (AI) can help a small country like El Salvador grow.
Historical Context and Economic Challenges
El Salvador has faced significant economic challenges over the past few decades, including poverty, gang violence, and a heavy reliance on remittances from abroad. The economy has traditionally been rooted in agriculture, with coffee and sugar being key exports. However, President Bukele, who took office on June 1, 2019, has sought to address these challenges by diversifying the economy and embracing technology as a key driver of growth.
Bukele’s Vision for Economic Transformation
President Bukele’s administration has prioritized technological innovation as a catalyst for economic transformation. His vision is to modernize the country’s infrastructure and position El Salvador as a hub for technological innovation in Latin America. This vision includes the strategic shift from an agriculture-based economy to one focused on technology, financial services, and tourism. The goal is to create a more resilient and diverse economic base that can sustain long-term growth and development.
The Adoption of Bitcoin as Legal Tender
One of the most groundbreaking moves by Bukele’s administration was the introduction of the Bitcoin Law, passed by the Legislative Assembly on June 9, 2021. This law made Bitcoin legal tender alongside the US dollar, which had been the country’s official currency since 2001. The rationale behind this decision was multifaceted:
- Financial Inclusion: With a significant portion of the population lacking access to traditional banking services, Bitcoin offers an alternative means of financial inclusion.
- Reduction in Remittance Costs: Remittances make up a substantial part of El Salvador’s economy. Bitcoin’s adoption aims to reduce the high transaction fees associated with remittance services.
- Economic Innovation: By adopting Bitcoin, El Salvador aims to attract foreign investment and position itself as a leader in cryptocurrency and blockchain technology.
The implementation of Bitcoin involved launching the Chivo Wallet, a state-sponsored digital wallet designed to facilitate Bitcoin transactions. The government also incentivized adoption by offering $30 worth of Bitcoin to citizens who registered for the wallet.
Initial Reactions and Impact
The reaction to the Bitcoin Law was mixed. While some praised the move as innovative and forward-thinking, others raised concerns about the volatility of Bitcoin and its potential impact on the economy. Despite these concerns, the Bukele administration has remained committed to its Bitcoin strategy, continuing to invest in Bitcoin and integrate it into the national economy.
Digital Transformation Initiatives
I
n addition to Bitcoin adoption, El Salvador has partnered with global tech giants like Google to enhance its digital infrastructure. These partnerships aim to modernize government services, improve healthcare through telemedicine platforms, and revolutionize education by integrating AI-driven tools. For instance, Google’s collaboration with the Salvadoran government includes training government agencies on cloud technologies and developing platforms that allow interoperability between institutions.
Strategic Shift to Technology, Financial Services, and Tourism
President Bukele’s broader economic strategy involves shifting El Salvador’s economic focus from traditional agriculture to more dynamic and sustainable sectors like technology, financial services, and tourism. This shift aims to create high-value jobs, attract foreign investment, and build a more diversified economy.
- Technology: By investing in digital infrastructure and fostering a favorable environment for tech startups, El Salvador aims to become a regional tech hub.
- Financial Services: The adoption of Bitcoin and other fintech innovations is intended to transform the financial landscape, making it more inclusive and efficient.
- Tourism: Enhancing the country’s tourism sector, with initiatives to promote its natural beauty and cultural heritage, is another key pillar of Bukele’s economic strategy.
Conclusion and Future Prospects
El Salvador’s journey towards becoming a technological leader in Latin America is a testament to the transformative power of visionary leadership and innovative policies. Under President Bukele, the country has taken bold steps to embrace technology, from adopting Bitcoin to integrating AI into public services. This series of articles will delve deeper into these initiatives, exploring their impact, challenges, and the future prospects for El Salvador in the global technological landscape.
By understanding El Salvador’s technological revolution, we can gain insights into the potential for other nations to leverage technology for economic and social development. The next article in this series will focus on the detailed implementation of Bitcoin as legal tender, examining the steps taken by the Bukele administration and the outcomes observed so far.
This introductory article sets the stage for a comprehensive exploration of El Salvador’s technological transformation under President Bukele. The subsequent articles will provide in-depth analyses and propose potential AI legislation to ensure the country’s continued leadership in technology within Latin America.

by Joche Ojeda | Jul 3, 2024 | Uncategorized
Hey there, fellow developers! Today, let’s talk about a practice that can revolutionize the way we create, test, and perfect our software: dogfooding. If you’re wondering what dogfooding means, don’t worry, it’s not about what you feed your pets. In the tech world, “eating your own dog food” means using the software you develop in your day-to-day operations. Let’s dive into how this can be a game-changer for us.
Why Should We Dogfood?
- Catch Bugs Early: By using our own software, we become our first line of defense against bugs and glitches. Real-world usage uncovers issues that might slip through traditional testing. We get to identify and fix these problems before they ever reach our users.
- Enhance Quality Assurance: There’s no better way to ensure our software meets high standards than by relying on it ourselves. When our own work depends on our product, we naturally aim for higher quality and reliability.
- Improve User Experience: When we step into the shoes of our users, we experience firsthand what works well and what doesn’t. This unique perspective allows us to design more intuitive and user-friendly software.
- Create a Rapid Feedback Loop: Using our software internally means continuous and immediate feedback. This quick loop helps us iterate faster, refining features and squashing bugs swiftly.
- Build Credibility and Trust: When we show confidence in our software by using it ourselves, it sends a strong message to our users. It demonstrates that we believe in what we’ve created, enhancing our credibility and trustworthiness.
Real-World Examples
- Microsoft: They’re known for using early versions of Windows and Office within their own teams. This practice helps them catch issues early and improve their products before public release.
- Google: Googlers use beta versions of products like Gmail and Chrome. This internal testing helps them refine their offerings based on real-world use.
- Slack: Slack’s team relies on Slack for communication, constantly testing and improving the platform from the inside.
How to Start Dogfooding
- Integrate it Into Daily Work: Start by using your software for internal tasks. Whether it’s a project management tool, a communication app, or a new feature, make it part of your team’s daily routine.
- Encourage Team Participation: Get everyone on board. The more diverse the users, the more varied the feedback. Encourage your team to report bugs, suggest improvements, and share their experiences.
- Set Up Feedback Channels: Create dedicated channels for feedback. This could be as simple as a Slack channel or a more structured feedback form. Ensure that the feedback loop is easy and accessible.
- Iterate Quickly: Use the feedback to make quick improvements. Prioritize issues that affect usability and functionality. Show your team that their feedback is valued and acted upon.
Overcoming Challenges
- Avoid Bias: While familiarity is great, it can also lead to bias. Pair internal testing with external beta testers to get a well-rounded perspective.
- Manage Resources: Smaller teams might find it challenging to allocate resources for internal use. Start small and gradually integrate more aspects of your software into daily use.
- Consider Diverse Use Cases: Remember, your internal environment might not replicate all the conditions your users face. Keep an eye on diverse scenarios and edge cases.
Conclusion
Dogfooding is more than just a quirky industry term. It’s a powerful practice that can elevate the quality of our software, speed up our development cycles, and build stronger trust with our users. By using our software as our customers do, we gain invaluable insights that can lead to better, more reliable products. So, let’s embrace the dogfood, turn our critical eye inward, and create software that we’re not just proud of but genuinely rely on. Happy coding, and happy dogfooding! ??
Feel free to share your dogfooding experiences in the comments below. Let’s learn from each other and continue to improve our craft together!
by Joche Ojeda | Jun 25, 2024 | Object-Oriented Programming
Aristotle and the “Organon”: Foundations of Logical Thought
Aristotle, one of the greatest philosophers of ancient Greece, made substantial contributions to a wide range of fields, including logic, metaphysics, ethics, politics, and natural sciences. Born in 384 BC, Aristotle was a student of Plato and later became the tutor of Alexander the Great. His works have profoundly influenced Western thought for centuries.
One of Aristotle’s most significant contributions is his collection of works on logic known as the “Organon.” This term, which means “instrument” or “tool” in Greek, reflects Aristotle’s view that logic is the tool necessary for scientific and philosophical inquiry. The “Organon” comprises six texts:
- Categories: Classification of terms and predicates.
- On Interpretation: Relationship between language and logic.
- Prior Analytics: Theory of syllogism and deductive reasoning.
- Posterior Analytics: Nature of scientific knowledge.
- Topics: Methods for constructing and deconstructing arguments.
- On Sophistical Refutations: Identification of logical fallacies.
Together, these works lay the groundwork for formal logic, providing a systematic approach to reasoning that is still relevant today.
Object-Oriented Programming (OOP): Building Modern Software
Now, let’s fast-forward to the modern world of software development. Object-Oriented Programming (OOP) is a programming paradigm that has revolutionized the way we write and organize code. At its core, OOP is about creating “objects” that combine data and behavior. Here’s a quick rundown of its fundamental concepts:
- Classes and Objects: A class is a blueprint for creating objects. An object is an instance of a class, containing data (attributes) and methods (functions that operate on the data).
- Inheritance: This allows a class to inherit properties and methods from another class, promoting code reuse.
- Encapsulation: This principle hides the internal state of objects and only exposes a controlled interface, ensuring modularity and reducing complexity.
- Polymorphism: This allows objects to be treated as instances of their parent class rather than their actual class, enabling flexible and dynamic behavior.
- Abstraction: This simplifies complex systems by modeling classes appropriate to the problem.
Bridging Ancient Logic with Modern Programming
You might be wondering, how do Aristotle’s ancient logical works relate to Object-Oriented Programming? Surprisingly, they share some fundamental principles!
- Categorization and Classes:
- Aristotle: Categorized different types of predicates and subjects to understand their nature.
- OOP: Classes categorize data and behavior, helping organize and structure code.
- Propositions and Methods:
- Aristotle: Propositions form the basis of logical arguments.
- OOP: Methods define the behaviors and actions of objects, forming the basis of interactions in software.
- Systematic Organization:
- Aristotle: His systematic approach to logic ensures consistency and coherence.
- OOP: Organizes code in a modular and systematic way, promoting maintainability and scalability.
- Error Handling:
- Aristotle: Identified and corrected logical fallacies to ensure sound reasoning.
- OOP: Debugging involves identifying and fixing errors in code, ensuring reliability.
- Modularity and Encapsulation:
- Aristotle: His logical categories and propositions encapsulate different aspects of knowledge, ensuring clarity.
- OOP: Encapsulation hides internal states and exposes a controlled interface, managing complexity.
Conclusion: Timeless Principles
Both Aristotle’s “Organon” and Object-Oriented Programming aim to create structured, logical, and efficient systems. While Aristotle’s work laid the foundation for logical reasoning, OOP has revolutionized software development with its systematic approach to code organization. By understanding the parallels between these two, we can appreciate the timeless nature of logical and structured thinking, whether applied to ancient philosophy or modern technology.
In a world where technology constantly evolves, grounding ourselves in the timeless principles of logical organization can help us navigate and create with clarity and precision. Whether you’re structuring an argument or designing a software system, these principles are your trusty tools for success.

by Joche Ojeda | Jun 21, 2024 | Database
Understanding ASCII vs. UTF-8 in Database Queries: A Practical Guide
When dealing with databases, understanding how different character encodings impact queries is crucial. Two common encoding standards are ASCII and UTF-8. This blog post delves into their differences, how they affect case-sensitive queries, and provides practical examples to illustrate these concepts.
ASCII vs. UTF-8: What’s the Difference?
ASCII (American Standard Code for Information Interchange)
- Description: A character encoding standard using 7 bits to represent each character, allowing for 128 unique symbols. These include control characters (like newline), digits, uppercase and lowercase English letters, and some special symbols.
- Range: 0 to 127.
UTF-8 (8-bit Unicode Transformation Format)
- Description: A variable-width character encoding capable of encoding all 1,112,064 valid character code points in Unicode using one to four 8-bit bytes. UTF-8 is backward compatible with ASCII.
- Range: Can represent characters in a much wider range, including all characters in all languages, as well as many symbols and special characters.
ASCII and UTF-8 Position Examples
Let’s compare the positions of some characters in both ASCII and UTF-8:
| Character |
ASCII Position |
UTF-8 Position |
| A |
65 |
65 |
| B |
66 |
66 |
| … |
… |
… |
| Y |
89 |
89 |
| Z |
90 |
90 |
| [ |
91 |
91 |
| \ |
92 |
92 |
| ] |
93 |
93 |
| ^ |
94 |
94 |
| _ |
95 |
95 |
| ` |
96 |
96 |
| a |
97 |
97 |
| b |
98 |
98 |
| … |
… |
… |
| y |
121 |
121 |
| z |
122 |
122 |
| Last ASCII (DEL) |
127 |
127 |
| ÿ |
Not present |
195 191 (2 bytes) |
Case Sensitivity in Database Queries
Case sensitivity can significantly impact database queries, as different encoding schemes represent characters differently.
ASCII Example
-- Case-sensitive query in ASCII-encoded database
SELECT * FROM users WHERE username = 'Alice';
-- This will not return rows with 'alice', 'ALICE', etc.
UTF-8 Example
-- Case-sensitive query in UTF-8 encoded database
SELECT * FROM users WHERE username = 'Ålice';
-- This will not return rows with 'ålice', 'ÅLICE', etc.
Practical Example with Positions
For ASCII, the characters included in the range >= 'A' and <= 'z' are:
A has a position of 65.a has a position of 97.
In a case-sensitive search, these positions are distinct, so A is not equal to a.
For UTF-8, the characters included in this range are the same since UTF-8 is backward compatible with ASCII for characters in this range.
Query Example
Let’s demonstrate a query example for usernames within the range >= 'A' and <= 'z'.
-- Query for usernames in the range 'A' to 'z'
SELECT * FROM users WHERE username >= 'A' AND username <= 'z';
Included Characters
Based on the ASCII positions, the range >= 'A' and <= 'z' includes:
- All uppercase letters:
A to Z (positions 65 to 90)
- Special characters:
[, \, ], ^, _, and ` (positions 91 to 96)
- All lowercase letters:
a to z (positions 97 to 122)
Practical Example with Positions
Given the following table:
-- Create a table
CREATE TABLE users (
id INT PRIMARY KEY,
username VARCHAR(255) CHARACTER SET utf8 COLLATE utf8_bin
);
-- Insert some users
INSERT INTO users (id, username) VALUES (1, 'Alice'); -- A = 65, l = 108, i = 105, c = 99, e = 101
INSERT INTO users (id, username) VALUES (2, 'alice'); -- a = 97, l = 108, i = 105, c = 99, e = 101
INSERT INTO users (id, username) VALUES (3, 'Ålice'); -- Å = 195 133, l = 108, i = 105, c = 99, e = 101
INSERT INTO users (id, username) VALUES (4, 'ålice'); -- å = 195 165, l = 108, i = 105, c = 99, e = 101
INSERT INTO users (id, username) VALUES (5, 'Z'); -- Z = 90
INSERT INTO users (id, username) VALUES (6, 'z'); -- z = 122
INSERT INTO users (id, username) VALUES (7, 'ÿ'); -- ÿ = 195 191
INSERT INTO users (id, username) VALUES (8, '_special');-- _ = 95, s = 115, p = 112, e = 101, c = 99, i = 105, a = 97, l = 108
INSERT INTO users (id, username) VALUES (9, 'example'); -- e = 101, x = 120, a = 97, m = 109, p = 112, l = 108, e = 101
Query Execution
-- Execute the query
SELECT * FROM users WHERE username >= 'A' AND username <= 'z';
Query Result
This query will include the following usernames based on the range:
Alice (A = 65, l = 108, i = 105, c = 99, e = 101)Z (Z = 90)example (e = 101, x = 120, a = 97, m = 109, p = 112, l = 108, e = 101)_special (_ = 95, s = 115, p = 112, e = 101, c = 99, i = 105, a = 97, l = 108)alice (a = 97, l = 108, i = 105, c = 99, e = 101)z (z = 122)
However, it will not include:
Ålice (Å = 195 133, l = 108, i = 105, c = 99, e = 101, outside the specified range)ålice (å = 195 165, l = 108, i = 105, c = 99, e = 101, outside the specified range)ÿ (ÿ = 195 191, outside the specified range)
Conclusion
Understanding the differences between ASCII and UTF-8 character positions and ranges is crucial when performing case-sensitive queries in databases. For example, querying for usernames within the range >= 'A' and <= 'z' will include a specific set of characters based on their ASCII positions, impacting which rows are returned in your query results.
By grasping these concepts, you can ensure your database queries are accurate and efficient, especially when dealing with different encoding schemes.
by Joche Ojeda | Jun 21, 2024 | Database, ORM
Why Compound Keys in Database Tables Are No Longer Valid
Introduction
In the realm of database design, compound keys were once a staple, largely driven by the need to adhere to normalization forms. However, the evolving landscape of technology and data management calls into question the continued relevance of these multi-attribute keys. This article explores the reasons why compound keys may no longer be the best choice and suggests a shift towards simpler, more maintainable alternatives like object identifiers (OIDs).
The Case Against Compound Keys
Complexity in Database Design
- Normalization Overhead: Historically, compound keys were used to satisfy normalization requirements, ensuring minimal redundancy and dependency. While normalization is still important, the rigidity it imposes can lead to overly complex database schemas.
- Business Logic Encapsulation: When compound keys include business logic, they can create dependencies that complicate data integrity and maintenance. Changes in business rules often necessitate schema alterations, which can be cumbersome.
Maintenance Challenges
- Data Integrity Issues: Compound keys can introduce challenges in maintaining data integrity, especially in large and complex databases. Ensuring the uniqueness and consistency of multi-attribute keys can be error-prone.
- Performance Concerns: Queries involving compound keys can become less efficient, as indexing and searching across multiple columns can be more resource-intensive compared to single-column keys.
The Shift Towards Object Identifiers (OIDs)
Simplified Design
- Single Attribute Keys: Using OIDs as primary keys simplifies the schema. Each row can be uniquely identified by a single attribute, making the design more straightforward and easier to understand.
- Decoupling Business Logic: OIDs help in decoupling the business logic from the database schema. Changes in business rules do not necessitate changes in the primary key structure, enhancing flexibility.
Easier Maintenance
- Improved Data Integrity: With a single attribute as the primary key, maintaining data integrity becomes more manageable. The likelihood of key conflicts is reduced, simplifying the validation process.
- Performance Optimization: OIDs allow for more efficient indexing and query performance. Searching and sorting operations are faster and less resource-intensive, improving overall database performance.
Revisiting Normalization
Historical Context
- Storage Constraints: Normalization rules were developed when data storage was expensive and limited. Reducing redundancy and optimizing storage was paramount.
- Modern Storage Solutions: Today, storage is relatively cheap and abundant. The strict adherence to normalization may not be as critical as it once was.
Balancing Act
- De-normalization for Performance: In modern databases, a balance between normalization and de-normalization can be beneficial. De-normalization can improve performance and simplify query design without significantly increasing storage costs.
- Practical Normalization: Applying normalization principles should be driven by practical needs rather than strict adherence to theoretical models. The goal is to achieve a design that is both efficient and maintainable.
ORM Design Preferences
Object-Relational Mappers (ORMs)
- Design with OIDs in Mind: Many ORMs, such as XPO from DevExpress, were originally designed to work with OIDs rather than compound keys. This preference simplifies database interaction and enhances compatibility with object-oriented programming paradigms.
- Support for Compound Keys: Although these ORMs support compound keys, their architecture and default behavior often favor the use of single-column OIDs, highlighting the practical advantages of simpler key structures in modern application development.
Conclusion
The use of compound keys in database tables, driven by the need to fulfill normalization forms, may no longer be the best practice in modern database design. Simplifying schemas with object identifiers can enhance maintainability, improve performance, and decouple business logic from the database structure. As storage becomes less of a constraint, a pragmatic approach to normalization, balancing performance and data integrity, becomes increasingly important. Embracing these changes, along with leveraging ORM tools designed with OIDs in mind, can lead to more robust, flexible, and efficient database systems.

by Joche Ojeda | Jun 11, 2024 | Uncategorized
Getting Started with Stratis Blockchain Development: Running Your First Stratis Node
Stratis is a powerful and flexible blockchain development platform designed to enable businesses and developers to build, test, and deploy blockchain applications with ease. If you’re looking to start developing for the Stratis blockchain, the first crucial step is to run a Stratis node. This article will guide you through the process, providing a clear and concise roadmap to get your development journey underway.
Introduction to Stratis Blockchain
Stratis offers a blockchain-as-a-service (BaaS) platform, which simplifies the development, deployment, and maintenance of blockchain solutions. Built on a foundation of the C# programming language and the .NET framework, Stratis provides an accessible environment for developers familiar with these technologies. Key features of Stratis include smart contracts, sidechains, and full node capabilities, all designed to streamline blockchain development and integration.
Why Run a Stratis Node?
Running a Stratis node is essential for several reasons:
- Network Participation: Nodes form the backbone of the blockchain network, validating and relaying transactions.
- Development and Testing: A local node provides a controlled environment for testing and debugging blockchain applications.
- Decentralization: By running a node, you contribute to the decentralization and security of the Stratis network.
Prerequisites
Before setting up a Stratis node, ensure you have the following:
- A computer with a modern operating system (Windows, macOS, or Linux).
- .NET Core SDK installed.
- Sufficient disk space (at least 10 GB) for the blockchain data.
- A stable internet connection.
Step-by-Step Guide to Running a Stratis Node
1. Install .NET Core SDK
First, install the .NET Core SDK, which is necessary to run the Stratis Full Node. You can download it from the official .NET Core website. Follow the installation instructions for your specific operating system. I recommend having all DotNetCore SDKs because the source code for most of the Stratis solutions target really an old framework version like.NET Core 2.1 so it’s better to have multiple choices of framework in case you need to re-target for compatibility
.NET Core Versions
- .NET Core 3.1 (LTS)
- .NET Core 3.0
- .NET Core 2.2
- .NET Core 2.1 (LTS)
- .NET Core 2.0
- .NET Core 1.1
- .NET Core 1.0
Installation Links
Download .NET Core SDKs
2. Clone the Stratis Full Node Repository
Next, clone the Stratis Full Node repository from GitHub. Open a terminal or command prompt and run the following command:
git clone https://github.com/stratisproject/StratisFullNode.git
This command will download the latest version of the Stratis Full Node source code to your local machine.
3. Build the Stratis Full Node
Navigate to the directory where you cloned the repository:
cd StratisFullNode
Now, build the Stratis Full Node using the .NET Core SDK:
dotnet build
This command compiles the source code and prepares it for execution.
4. Run the Stratis Full Node
Once the build process is complete, you can start the Stratis Full Node. Use the following command to run the node:
cd Stratis.StraxD
dotnet run -testnet
This will initiate the Stratis node, which will start synchronizing with the Stratis blockchain network.
5. Verify Node Synchronization
After starting the node, you need to ensure it is synchronizing correctly with the network. You can check the node’s status by visiting the Stratis Full Node’s API endpoint in your web browser:
http://localhost:37221/api
here is more information about the possible ports for the API depending on which network you want to use (test or main) and which command did you use to start up the API
Swagger
To run the API in a specific port you can use the following code
StraxTest (dotnet run -testnet -apiport=38221)
http://localhost:38221/Swagger/index.html
StraxTest
http://localhost:27103/Swagger
StraxMain
http://localhost:17103/Swagger
You should see a JSON response indicating the node’s current status, including its synchronization progress.
Conclusion
Congratulations! You have successfully set up and run your first Stratis node. This node forms the foundation for your development activities on the Stratis blockchain. With your node up and running, you can now explore the various features and capabilities of the Stratis platform, including deploying smart contracts, interacting with sidechains, and building blockchain applications.
As you continue your journey, remember that the Stratis community and its comprehensive documentation are valuable resources. Engage with other developers, seek guidance, and contribute to the growing ecosystem of Stratis-based solutions. Happy coding!
Previous articles
Discovering the Simplicity of C# in Blockchain Development with Stratis | Joche Ojeda










